Ordinary Internet users frequently are scolded for choosing weak, easily-guessed passwords. New research suggests that hackers in the cyber underground are also likely to pick lame passwords for their favorite online forums.
Antichat.ru, a Russian language hacker forum that has attracted more than 41,000 users since its founding nearly a decade ago. By matching the user names in the database with those listed in the public pages of the forum, I discovered that I’d been given a snapshot of all Antichat user information and private messages prior to June 2010, when Antichat.ru apparently experienced a forum compromise.
I wanted to match the Antichat user names, associated email and ICQ addresses with those of other forums for which I’ve collected user databases. I also wanted to see how many of the passwords were easily crackable. To do this, I enlisted the help of an anti-spam source that has access to some serious hardware and software capable of cracking thousands of passwords per hour.
More than 18,000 of the 41,037 passwords in the database were crackable within a few days. 4,500 passwords were used by five or more individual users.
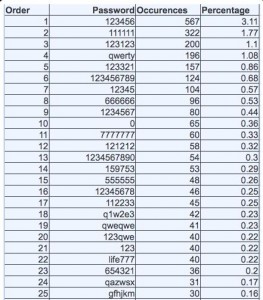
The most easily-guessed passwords were six characters long or less, and 75 percent of the top 20 most common simple passwords were uncomplicated number strings. More than three percent of Antichat users whose passwords were cracked (567) picked one of the simplest passwords, “123456″; 1.77 percent (322) chose “111111″; Just over 1 percent selected “123123″. Another 196 users opted for “qwerty,” a common meme easily typed from left to right across a keyboard. Sixty-five Antichat users picked a single-character password: “0.”
Although nearly half of the Antichat user passwords were crackable, the passwords aren’t useful for gaining access to Antichat user accounts: Forum administrators have changed the site’s login process to automatically tie the user’s credentials to his or her Internet address. However, the Internet address data tied to each account may be of interest to law enforcement investigators.
Top 25 most-used Antichat passwords.
The Antichat database also included many private messages that forum users sent to each other. Most of these messages are short, banal or unremarkable (e.g., “How do I get this bot working right?”); others appear to involve more serious transactions, including the theft of sensitive personal and financial data from organizations and individuals.
The hardware used to crack the Antichat passwords was an EVGA GTX 295 graphics card running Hashcat software under CUDA. The Antichat forum runs on Vbulletin 3.0, which uses a salted hash to add complexity to stored passwords. Depending on the approach used, the number of hashed passwords processed in an hour ranges between approx 1,000 – 7,000, this compares with many billions of permutations per hour on unsalted hashes.
The number ‘cracked’ per hour depends on the complexity of the passwords and the method of attack being used. My anti-spam associate worked on this hash list for about 18 days, operating 24/7. The total number cracked is 18,225 of 41,037, or 44% of the total.
It may be that many Antichat users weren’t worried about picking strong passwords because they didn’t care whether their accounts got hacked. But it’s important that KrebsOnSecurity readers understand the basic principles for picking strong passwords and for avoiding practices that lead to weak and easily-cracked passwords. Take a look at my password primer

The Antichat database also included many private messages that forum users sent to each other. Most of these messages are short, banal or unremarkable (e.g., “How do I get this bot working right?”); others appear to involve more serious transactions, including the theft of sensitive personal and financial data from organizations and individuals.
The hardware used to crack the Antichat passwords was an EVGA GTX 295 graphics card running Hashcat software under CUDA. The Antichat forum runs on Vbulletin 3.0, which uses a salted hash to add complexity to stored passwords. Depending on the approach used, the number of hashed passwords processed in an hour ranges between approx 1,000 – 7,000, this compares with many billions of permutations per hour on unsalted hashes.
The number ‘cracked’ per hour depends on the complexity of the passwords and the method of attack being used. My anti-spam associate worked on this hash list for about 18 days, operating 24/7. The total number cracked is 18,225 of 41,037, or 44% of the total.
It may be that many Antichat users weren’t worried about picking strong passwords because they didn’t care whether their accounts got hacked. But it’s important that KrebsOnSecurity readers understand the basic principles for picking strong passwords and for avoiding practices that lead to weak and easily-cracked passwords. Take a look at my password primer

breach the security I am impressed. I don't think Ive met anyone who knows as much about this subject as you do. You are truly well informed and very intelligent. You wrote something that people could understand and made the subject intriguing for everyone. Really, great blog you have got here.
ReplyDelete